Your donation will support the student journalists of Iowa City High School. For 2023, we are trying to update our video and photo studio, purchase new cameras and attend journalism conferences.
Dangers of The Dark Web
April 26, 2017
 As the internet continues to evolve, so does anonymity. As more and more daily interactions move online, worry grows about how closely monitored social media and the web are.
As the internet continues to evolve, so does anonymity. As more and more daily interactions move online, worry grows about how closely monitored social media and the web are.
“It’s pretty scary that everything you do on the Internet can be traced back to you,” said City High student Max*. “People like their privacy, and the dark web gives people that option to stay anonymous.”
Max, like many other students, does not go on the dark web for the purpose of using the illegal services. A sense of adrenaline can be felt when one is doing something they shouldn’t be.
“I feel like a lot of people go on the dark web just for fun with friends, to see all of the illegal things on there. There’s a certain rush you get from seeing all of the things on there,” Said Max. “It’s kind of scary though. I’ve seen some really disturbing stuff on there like videos of people getting killed, websites selling crazy drugs and guns, and weird animal porn.”
The dark web has been available to the public since the release of Tor (a web browser that protects the anonymity of users) in 2003, but as technology continues to grow criminals are finding ways to use the dark web for illicit purposes. With new ways to stay anonymous online, illegal web activities are on the rise. Purchasing drugs, hiring hit-men, and viewing child pornography are just a number of things that can be done on the dark web.
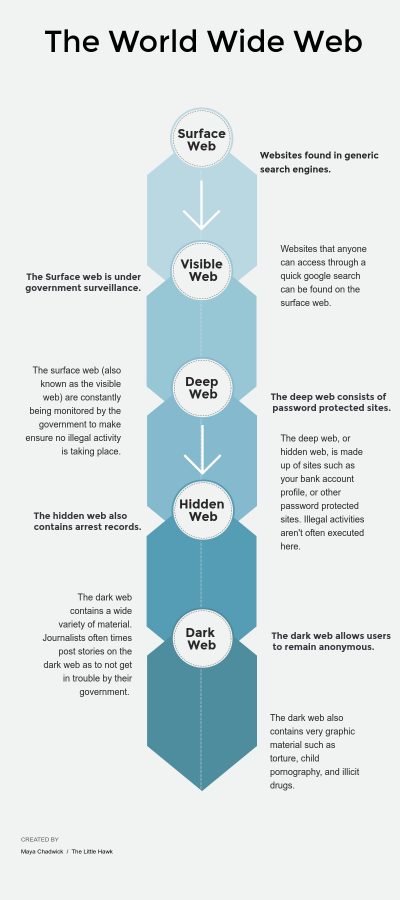
There are three basic levels to the world wide web. There’s the surface web, the deep web, and the dark web.
The surface web is the portion of the web that is available to anyone and is accessible through search engines such as Google, Bing, or Yahoo.
The deep web is the portion of the web can’t be found by googling it, such as password protected webpages.
The dark web is an end to end encrypted version of the web that allows browsers to remain anonymous. The dark web can be accessed by using a program called Tor, which protects the anonymity of the browser.
“It’s the same protocols, the same HTML, the same code and everything except when you’re visiting the dark web, supposedly all of the traffic is encrypted on each end of the relay so that you get an anonymized version of the web.” Dustin Quam, head web developer with the University of Iowa Marketing + Design, said.
Users are able to stay anonymous while browsing with Tor due to encryption on the client end. The currency used to purchase things on the dark web, called Bitcoins, also aids to the anonymity of the dark web.
“You go to what’s called ‘onion websites’ because there are layers of encryption that are coming off as you exit a relay node, but there’s some controversy with the reliability of the relay nodes.” Quam said.
In essence, relay nodes are connections points where data can be received, stored, or sent through networks. On the dark web, as you go onto different website there are different levels of privacy, but the security of different relay nodes, or connection points, can be difficult to determine.
Onion websites are the same code wise as any other website that one would find on the surface web. The difficulty with actually uploading .onion websites comes when trying to find a third party to host the website.
“[The ability to host illegal websites on the dark web] depends on how willing people are to do those bad things,” Said Quam. “It’s not that hard, there’s nothing really different about hosting something like that code-wise, it’s finding the hosting or finding a Tor enabled server to host it that’s the hard part.”
While the dark web is used for illegal activities, there are many sites on the dark web that do not host illegal activity, such as chat rooms or websites that provide a “safe-place” for people with fetishes that are seen as strange or taboo. The dark web also gives journalists a place to leak information on corruption in their countries. However, illegal activity on the dark web is very real. Disturbing images of bestiality, rape, and murder can be found on the dark web.
“There’s a lot of nasty stuff on the dark web but on the other hand, the dark web is kind of a locked room essentially where private things can happen which can be good for developing nations that need to leak information about corrupt politicians,” Quam said. “Tor and the dark web can be considered champions of privacy probably, law enforcement people would never say that, but I think that there’s definitely good in there somewhere. It’s not primarily used for good right now, but there is good.”
Dustin Quam has had firsthand experience with the dark side of the dark web. Around 8 years ago, a friend of Quam’s used the dark web to illegally purchase drugs. Law enforcement never knew about this transaction.
The Iowa City Police Department does what they can to protect against online crimes, but they aren’t the ones who are browsing the dark web and looking specifically for local online crimes. The FBI, NSA, and CIA work to track down the criminals hosting illegal websites, and if they’re being hosted from Iowa City, the police department is notified.
While illegal web activity isn’t something new, it’s still very prevalent in society.
“We’ve had a couple of cases just this month dealing with the internet. [Technology] has pushed a lot of criminal industries into the internet versus on our streets,” said Sergeant Bailey. “As technology has grown so has the ability to commit crimes and to, more importantly, remain anonymous in committing those crimes.”
The dark web gained publicity back in 2013 when an online blackmarket called Silk Road was shut down by the FBI. Silk Road was launched in 2011, and offered a variety of services. To name a few, there were hitmen for hire, information on hacking, and drugs ranging from prescription drugs to methamphetamine. An informant notified police about the website, and soon an investigation began. The DEA and FBI worked to track down the administrators of the website and the sellers, and eventually many were captured and the website was abolished.
“I think [law enforcement] is doing all that they can [to shut down illegal websites]. The NSA and the CIA are always figuring out how to break Tor basically,” said Quam. “The thing about encryption though is that, if you have something that is fundamentally secure mathematically, it becomes a giant challenge to keep up with that. And if it’s 100% secure, which nothing is, but if it is 99% secure, they have to figure out a way to break encryption which is a mathematically hard thing to do.”
*Name of student has been changed to protect their identity.